XLMRat Lab
CyberDefenders Network Forensics Lab

Scenario
A compromised machine has been flagged due to suspicious network traffic. Your task is to analyze the PCAP file to determine the attack method, identify any malicious payloads, and trace the timeline of events. Focus on how the attacker gained access, what tools or techniques were used, and how the malware operated post-compromise.
Question 1
The attacker successfully executed a command to download the first stage of the malware. What is the URL from which the first malware stage was installed?
Answer 1
The attacker executes a GET request from the IP address 45.126.209.4 via port 222. Grabbing mdm.jpg.
Press enter or click to view image in full size

Question 2
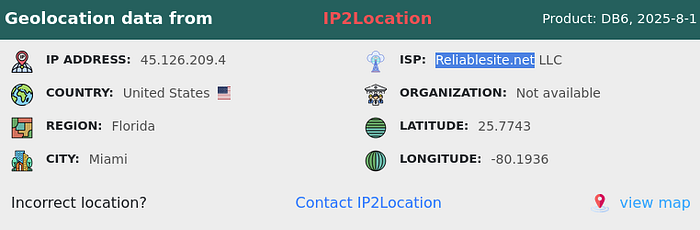
Which hosting provider owns the associated IP address?
Answer 2
A search for the IP address reveals the hosting provider is: Reliablesite.net.
Press enter or click to view image in full size
Question 3
By analyzing the malicious scripts, two payloads were identified: a loader and a secondary executable. What is the SHA256 of the malware executable?
Answer 3
This one was a little tough. I saw that the file had a LARGE hex string. Which cyberchef detected as a malware executable. However I can’t digest it unless I remove the “_” between each value.
Press enter or click to view image in full size

So using an online tool I was quickly able to replace _ with nothing. To get the whole string. After which I placed it into cyberchef to get the sha256.
Press enter or click to view image in full size

Question 4
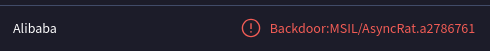
What is the malware family label based on Alibaba?
Answer 4
A VirusTotal search revealed AyncRat.
Question 5
What is the timestamp of the malware’s creation?
Answer 5

Question 6
Which LOLBin is leveraged for stealthy process execution in this script? Provide the full path.
Answer 6
Studying the code a little more, it was very clear that there was some rather heavy obfuscation going on.
Press enter or click to view image in full size

However, looking at the 3rd and 4th line in the above screenshot. You can see that there is a windows file path directing towards RegSvcs.exe. It tries to obfuscate by breaking up words with the # symbol.
Question 7
The script is designed to drop several files. List the names of the files dropped by the script.
Answer 7
Looking through the rest of the code there are 3 files that are being dropped by the script.

Last updated