BlueSky Ransomware Lab
CyberDefenders Network Forensics Lab

Scenario
A high-profile corporation that manages critical data and services across diverse industries has reported a significant security incident. Recently, their network has been impacted by a suspected ransomware attack. Key files have been encrypted, causing disruptions and raising concerns about potential data compromise. Early signs point to the involvement of a sophisticated threat actor. Your task is to analyze the evidence provided to uncover the attacker’s methods, assess the extent of the breach, and aid in containing the threat to restore the network’s integrity.
Question 1
Knowing the source IP of the attack allows security teams to respond to potential threats quickly. Can you identify the source IP responsible for potential port scanning activity?
Answer 1
The packet capture that was provided reveals a large amount of port scanning by 87.96.21.84. Seen here:
Press enter or click to view image in full size
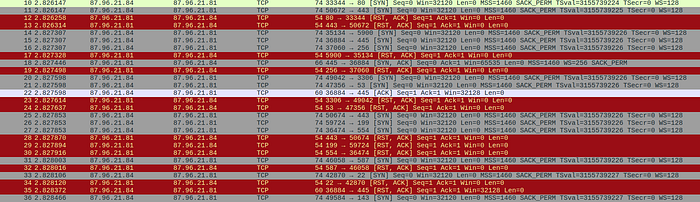
SYN signals a initiation in communication. the RST flag signifies the connection is down or the service is not taking requests. Easily colour coded in Wireshark.
Question 2
During the investigation, it’s essential to determine the account targeted by the attacker. Can you identify the targeted account username?
Answer 2
Here I was looking for a TDS packet, that is normally used for communication between clients and SQL databases. There were a ton of what looked to be failed log in attempts. But finding a successful one revealed the username that was targeted. sa.
Press enter or click to view image in full size

Question 3
We need to determine if the attacker succeeded in gaining access. Can you provide the correct password discovered by the attacker?
Answer 3
The same packet reveals the password that was used to log into the account.
Question 4
Attackers often change some settings to facilitate lateral movement within a network. What setting did the attacker enable to control the target host further and execute further commands?
Answer 4
Looking at a few packets after the first successful login reveals that the attacker tries to set up something to maintain their access to the victim. They look to spawn a cmdshell.
Press enter or click to view image in full size

Question 5
Process injection is often used by attackers to escalate privileges within a system. What process did the attacker inject the C2 into to gain administrative privileges?
Answer 5
For this task I needed to boot up my Windows VM and look at the Event Viewer logs. I filtered the logs to show only PowerShell, and reading and learning more about how Event Logs work. An Event ID with the value of 400 means a new instance of powershell spawning. So looking for those would narrow the search down.

Skimming through the logs, there are 3 host names that popup. ConsoleHost, Default Host and MSFConsole. There was only 1 instance of MSFConsole, which stood out to me and after doing some research on the topic it seems to be apart of the Metasploit Framework. A tool used by pen testers. The log also shows the Application it tries to use winlogon.exe. Which would be a perfect thing for an attacker to attached a C2 to.

Question 6
Following privilege escalation, the attacker attempted to download a file. Can you identify the URL of this file downloaded?
Answer 6
I used NetworkMiner here, looking in the file tabs once opened the pcap file. The first file the attacker downloads is called checking.ps1.
Press enter or click to view image in full size

Question 7
Understanding which group Security Identifier (SID) the malicious script checks to verify the current user’s privileges can provide insights into the attacker’s intentions. Can you provide the specific Group SID that is being checked?
Answer 7
NetworkMiner can be used to export the file, in fact when you open a pcap file it does this for you. So I am able to look inside the malicious script.
The first line in the script reveals a variable that is set to either true or false if the current group = one of the specified SIDs.
Question 8
Windows Defender plays a critical role in defending against cyber threats. If an attacker disables it, the system becomes more vulnerable to further attacks. What are the registry keys used by the attacker to disable Windows Defender functionalities? Provide them in the same order found.
Answer 8
Scrolling down further in the script, there is a function called StopAV. Containing the following code:
The script tries to find the registry keys within the target system related to Windows Defender.
Question 9
Can you determine the URL of the second file downloaded by the attacker?
Answer 9
The script also has a function that downloads a second payload. Which, judging by the name of the function and script, attempts to clean any sort of trace from the victims machine.
It also gives me the URL.
Question 10
Identifying malicious tasks and understanding how they were used for persistence helps in fortifying defenses against future attacks. What’s the full name of the task created by the attacker to maintain persistence?
Answer 10
Within the same function as shown above, it attempts to set up a schedule task via a Windows binary.
The tasks name is LPupdate, it then specifies it should activate through cmd.exe, and the file being del.ps1, the sets it to run hourly.
Question 11
Based on your analysis of the second malicious file, What is the MITRE ID of the main tactic the second file tries to accomplish?
Answer 11
The second file, del.ps1, attempts to stop any sort of process explorer that could be used to either stop the malware or analyze it.
The script itself is trying to evade defense measures that could be employed. Defense Evasion TA0005.
Question 12
What’s the invoked PowerShell script used by the attacker for dumping credentials?
Answer 12
Looking through the other files that were dumped it was easy to find a script that would be used for dumping credentials. It was named: Invoke-PowerDump.
Press enter or click to view image in full size

Interestingly it seems to have been a script the attacker had found online and used maliciously.
Question 13
Understanding which credentials have been compromised is essential for assessing the extent of the data breach. What’s the name of the saved text file containing the dumped credentials?
Answer 13
Browsing one of the other .ps1 files revealed that the usernames and password hashes were being dump into a file called hashes.txt.
Press enter or click to view image in full size

The script seems to sort the usernames and passwords and also download another file.
Question 14
Knowing the hosts targeted during the attacker’s reconnaissance phase, the security team can prioritize their remediation efforts on these specific hosts. What’s the name of the text file containing the discovered hosts?
Answer 14
The last remaining .ps1 file was called extracted_hosts.txt. A file with 4 IP addresses in, which judging by the other scripts is used to transport the data that had been dumped back to the attacker. Having multiple as back ups.
Press enter or click to view image in full size

Question 15
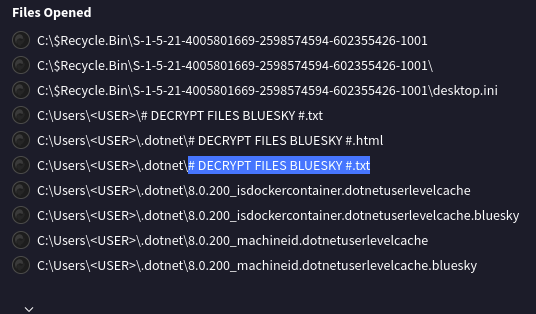
After hash dumping, the attacker attempted to deploy ransomware on the compromised host, spreading it to the rest of the network through previous lateral movement activities using SMB. You’re provided with the ransomware sample for further analysis. By performing behavioral analysis, what’s the name of the ransom note file?
Answer 15
Uploading the sample to VirusTotal shows a varity of files that are created and opened by the ransomware.
Question 16
In some cases, decryption tools are available for specific ransomware families. Identifying the family name can lead to a potential decryption solution. What’s the name of this ransomware family?
Answer 16
Looking at the popular threat label VirusTotal gives me after uploading the file gives me the answer: bluesky.
Press enter or click to view image in full size


Last updated