Lockdown Lab
CyberDefenders Network Forensics Lab

Scenario
TechNova Systems’ SOC has detected suspicious outbound traffic from a public-facing IIS server in its cloud platform — activity suggestive of a web-shell drop and covert connections to an unknown host.
As the forensic examiner, you have three critical artefacts in hand: a PCAP capturing the initial traffic, a full memory image of the server, and a malware sample recovered from disk. Reconstruct the intrusion and all of the attacker’s activities so TechNova can contain the breach and strengthen its defenses.
Question 1
After flooding the IIS host with rapid-fire probes, the attacker reveals their origin. Which IP address generated this reconnaissance traffic?
Answer 1
Knowing there was an attempt to flood I looked for a large amount of packets sent from a single IP address. Looking in WireShark in the conversation window I could see a ton originating from 10.0.2.4.

Question 2
Zeroing in on a single open service to gain a foothold, the attacker carries out targeted enumeration. Which MITRE ATT&CK technique ID covers this activity?
Answer 2
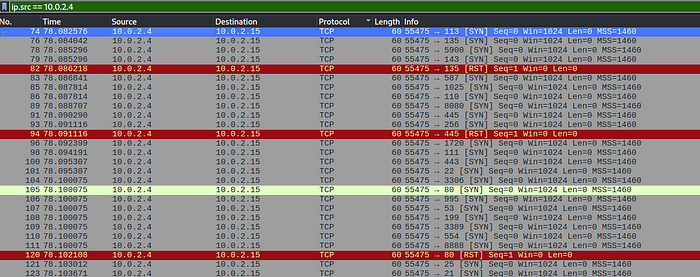
The attacker enumerates a ton of ports, looking for various services. Starting at packet 74. This would indicate that the MITRE ATT&CK ID would be T1046.
Press enter or click to view image in full size
Question 3
While reviewing the SMB traffic, you observe two consecutive Tree Connect requests that expose the first shares the intruder probes on the IIS host. Which two full UNC paths are accessed?
Answer 3
Filtering to just view the SMB2 traffic there are 2 requests. Then just using a simple CTRL+F and filtering for strings I was able to find both Tree Connect Request Tree’s.
Press enter or click to view image in full size

Question 4
Inside the share, the attacker plants a web-accessible payload that will grant remote code execution. What is the filename of the malicious file they uploaded, and what byte length is specified in the corresponding SMB2 Write Request?
Answer 4
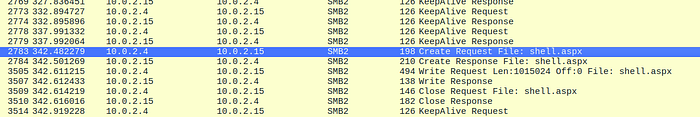
Looking through the same filtered packets, I was on the look out for any Create Request File strings in the information panel. There were a couple that didn’t stand out, such as information.txt. But a very obvious one appeared further down. shell.aspx. aspx files are used to create webpages.
Press enter or click to view image in full size

Question 5
The newly planted shell calls back to the attacker over an uncommon but firewall-friendly port. Which listening port did the attacker use for the reverse shell?
Answer 5
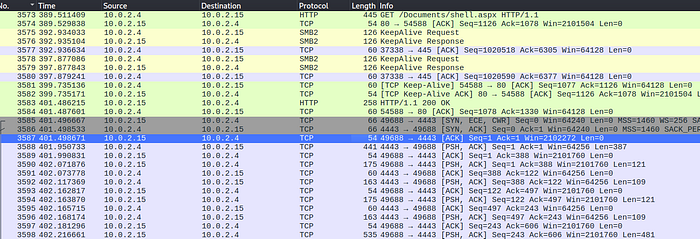
I first searched for a GET request that would trigger the reverse shell. Once I found that at packet number 3573, I looked to see if there was any unusual traffic from a specific port after its execution. Knowing the attackers IP address is 10.0.2.4 and the victims was 10.0.2.15, it was easy to see that port 4443 was the culprit here. As there was an unreal amount of connections between the 2 using 1 specific port.
Press enter or click to view image in full size
Question 6
Your memory snapshot captures the system’s kernel in situ, providing vital context for the breach. What is the kernel base address in the dump?
Answer 6
For the next few steps I will be using volatility3. After running the following command:
I was able to grab the kernel base address.
Question 7
A trusted service launches an unfamiliar executable residing outside the usual IIS stack, signalling a persistence implant. What is the final full on-disk path of that executable, and which MITRE ATT&CK persistence technique ID corresponds to this behaviour?
Answer 7
It took a couple of steps to narrow down what I was looking for. First of all I used the following:
Grabbing the process tree. From there I looked over each process to find anything that stands out. The first thing that I noticed was updatenow.exe, launching from the start menu. This in itself was suspicious, after looking it up online I found that it wasn’t a native windows exe.
After this, I used grep to narrow it down to find the path in which is executes from.
So the program executes at start up, which means it falls under T1547. Boot or Logon Autostart Execution.
Question 8
The reverse shell’s outbound traffic is handled by a built-in Windows process that also spawns the implanted executable. What is the name of this process, and what PID does it run under?
Answer 8
Looking back through the pstree output I found the following:
The * chars represent what is a child and a parent process. In this instance, updatenow.exe is a child process of w3wp.exe. Thus giving me the answer.
Question 9
Static inspection reveals the binary has been packed to hinder analysis. Which packer was used to obfuscate it?
Answer 9
A simple upload to virus total gives away a lot of information. UPX is the answer here.
Press enter or click to view image in full size

Question 10
Threat-intel analysis shows the malware beaconing to its command-and-control host. Which fully qualified domain name (FQDN) does it contact?
Answer 10
Looking at the relations tab within VirusTotal gives you the connected domains:

Question 11
Open-source intel associates that hash with a well-known commodity RAT. To which malware family does the sample belong?
Answer 11
VirusTotal gives a lot of information, including malware family names. This one turns out to be in the agenttesla family.


Last updated