Silent Breach Lab
CyberDefenders Endpoint Forensics Lab
Press enter or click to view image in full size

Scenario
The IMF is hit by a cyber attack compromising sensitive data. Luther sends Ethan to retrieve crucial information from a compromised server. Despite warnings, Ethan downloads the intel, which later becomes unreadable. To recover it, he creates a forensic image and asks Benji for help in decoding the files.
Question 1
What is the MD5 hash of the potentially malicious EXE file the user downloaded?
Answer 1
It looks like the user had downloaded a malicious file that was disguised as a .PDF file. A classic trick.

A simple exporting of the hash file within FTK Imager gave me the following:
Question 2
What is the URL from which the file was downloaded?
Answer 2
Chrome happened to be the browser that was used to download the file. Chrome stores history and other things in the following folder:
I found a history file within this but it didn’t lead to anything, only a single download for TeamViewer. So next I tried the same thing with Edge’s history file.
Press enter or click to view image in full size

The malicious file was downloaded from the following address:
Question 3
What application did the user use to download this file?
Answer 3
Microsoft Edge, since I found the download URL in the Edge history file.
Question 4
By examining Windows Mail artifacts, we found an email address mentioning three IP addresses of servers that are at risk or compromised. What are the IP addresses?
Answer 4
This one took a little digging within the file system and some research as to where Windows Mail artifacts are located.
Press enter or click to view image in full size
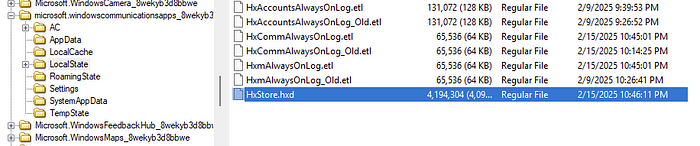
After extracting the above file, HxStore.hxd I had to download and run the strings utility and export the results to a file using the following command:
This produced a VERY large list of strings. Which I didn’t really want to search though, so I ended up uploading the file to CyberChef. Once uploaded, I used the IP addresses extractor feature.
Press enter or click to view image in full size

There are 3 IP addresses here, which is what I was looking for!
Question 5
By examining the malicious executable, we found that it uses an obfuscated PowerShell script to decrypt specific files. What predefined password does the script use for encryption?
Answer 5
After extrating the file from FTK Imager and defanging the file, I uploaded it to CyberChef to grab the strings. From here, I opened itup in NotePad++ in order to see the full output.
Knowing that I was looking for a PowerShell script, I searched for the .ps1 file extension and found the following:
Press enter or click to view image in full size

This appears, on the face, to be an obfuscation technique, joining 2 Base64 strings together, using random capitalization etc.
Working backwards here, I know I needed to get the code FROM Base64, but also reverse the values that were placed into a char array.
Press enter or click to view image in full size

Giving me the following:
Press enter or click to view image in full size

Question 6
After identifying how the script works, decrypt the files and submit the secret string.
Answer 6
This question was tough for me. I had to learn how the encryption worked from the output code. I did some research on how I might do this since I was rather stumped.
Above is the code. Here is the thought process for how I get the files decrypted and retrieve the secret phrase.
To note an iv in cryptography is used as an initial state, its supposed to be random but helps provide the same plaintext with different ciphertexts when encrypted multiple times. This is what I will focus on first, getting the value for key and iv.
The initial keySize value is set to 32, and ivSize is set to 16. I needed to look what to do after this step, but it turns out adding these together and then getting the bits value is what I needed to do. So 48 bytes = 384 bits.
Press enter or click to view image in full size
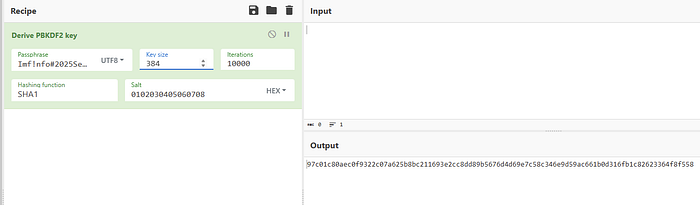
The first 32 bytes (64 chars) of this is the key, the last 16 (32 chars) is the iv value. Then moving on I needed to decrypt the AES function.
I can now move forward with decrypting the files that were present on the desktop of the machine. Using them as input in Cyberchef with the AES decrypt function.
Press enter or click to view image in full size

After doing the above I saved the output and opened the .pdf to get the final answer/secret message!
This was a really satisfying challenge. A little tough towards the end and I needed a couple of nudges, but I feel I learnt a lot about reversing encryption on files and more on dissecting code.
Last updated