RedLine Lab
CyberDefenders Endpoint Forensics Lab

Scenario
As a member of the Security Blue team, your assignment is to analyze a memory dump using Redline and Volatility tools. Your goal is to trace the steps taken by the attacker on the compromised machine and determine how they managed to bypass the Network Intrusion Detection System (NIDS). Your investigation will identify the specific malware family employed in the attack and its characteristics. Additionally, your task is to identify and mitigate any traces or footprints left by the attacker.
Question 1
What is the name of the suspicious process?
Answer 1
After using volatility3 to list all the processes that were running when the memory dump was captured, there were a couple of processes that I did not recognise. One of which being oneetx.exe. After a brief search it was clear that this was a form of malware.

Question 2
What is the child process name of the suspicious process?
Answer 2
Using the windows.pstree command, I could see that rundll32.exe processes had been spawned by the malware. Which is very common amongst many malware strains.
Question 3
What is the memory protection applied to the suspicious process memory region?
Answer 3
After using the following command:
I was able to find any sort of injected code by files during the memory dump. I found that oneetx.exe was using PAGE_EXECUTE_READWRITE. Which would be suspicious, since it could indicate code injection.
Press enter or click to view image in full size

Question 4
What is the name of the process responsible for the VPN connection?
Answer 4
While looking through the process tree output once more. tun2socks.exe caught my eye. It also showed up on a windows.netscan search. Indicating that it was part of a process to set up a VPN. Working my way up the process tree it was clear that Outline.exe was responsible for the VPN connection.

Question 5
What is the attacker’s IP address?
Answer 5
Using the windows.netscan command once again I was able to determine the attacker’s IP was 77.91.124.20. Since it was listed as a foregin address in the output, linking back to the malicious file.

Question 6
What is the full URL of the PHP file that the attacker visited?
Answer 6
After manually dumping the strings from the dump.mem file and searching for every instance of the attackers IP address within the file. I was able to find the .php file.
Question 7
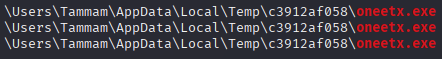
What is the full path of the malicious executable?
Answer 7
Using the following command:
I was able to find instances of the malicious exe file, including its location on the file system.

Last updated