KrakenKeylogger Lab
CyberDefenders Endpoint Forensics Lab
Press enter or click to view image in full size

Scenario
An employee at a large company was assigned a task with a two-day deadline. Realizing that he could not complete the task in that timeframe, he sought help from someone else. After one day, he received a notification from that person who informed him that he had managed to finish the assignment and sent it to the employee as a test. However, the person also sent a message to the employee stating that if he wanted the completed assignment, he would have to pay $160.
The helper’s demand for payment revealed that he was a threat actor. The company’s digital forensics team was called in to investigate and identify the attacker, determine the extent of the attack, and assess potential data breaches. The team must analyze the employee’s computer and communication logs to prevent similar attacks in the future.
Question 1
What is the the web messaging app the employee used to talk to the attacker?
Answer 1
I was unaware of this, but there is a database of windows notifications within the system. So I went digging into the follow path:
Looking at the Notification table within the database I found an entry on line 20 that hinted towards Telegram being used.

Question 2
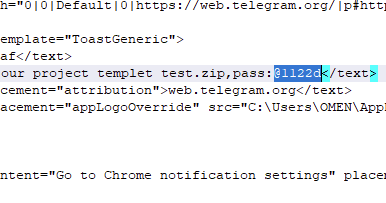
What is the password for the protected ZIP file sent by the attacker to the employee?
Answer 2
Within the same cell as the above question, the password is revealed in plaintext.
Question 3
What domain did the attacker use to download the second stage of the malware?
Answer 3
From here I needed to look into the malware that was sent by the attacker. There were 2 files within the zip archive.

The “templet.lnk” file was what I focused on first, since I am unable to look inside the .docx file. Using LECmd I was able to find some obfuscated code.
Press enter or click to view image in full size

I don’t normally like using AI for things since it feels like cheating, but for this one I slapped it into an LLM to see if it could help me deobfuscate the code. From just basic observations however, there is a jumbled up URL in the arguments of this .lnk file.
Once I looked over the results of the LLM output, I found that the code was reversing the string and taking 2 character chunks and swapping them around.
I did this manually, starting at the end of the URL and working backwards.
Question 4
What is the name of the command that the attacker injected using one of the installed LOLAPPS on the machine to achieve persistence?
Answer 4
I did some research on LOLAPPS, leaving of the land applications, and found that the user had GreenShot installed. A simple screenshot program. Which apparently had a way to gain persistence according to the website linked above.
Looking into the file path to the .ini file and looking over the external commands I found one that referenced the .lnk file from earlier.
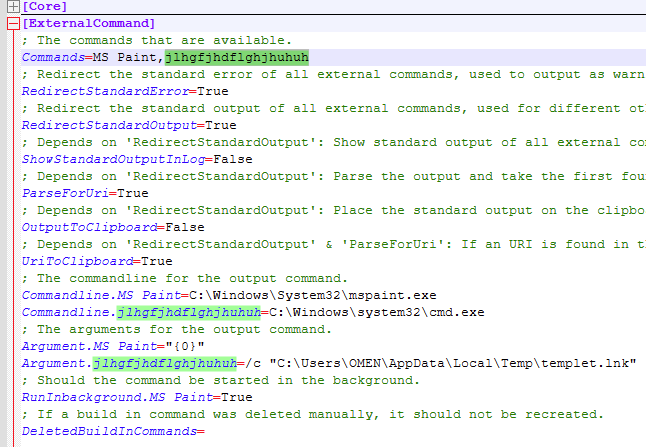
This would use the program to launch the malicious .lnk file.
Question 5
What is the complete path of the malicious file that the attacker used to achieve persistence?
Answer 5
The above screenshot gives the full file path.
Question 6
What is the name of the application the attacker utilized for data exfiltration?
Answer 6
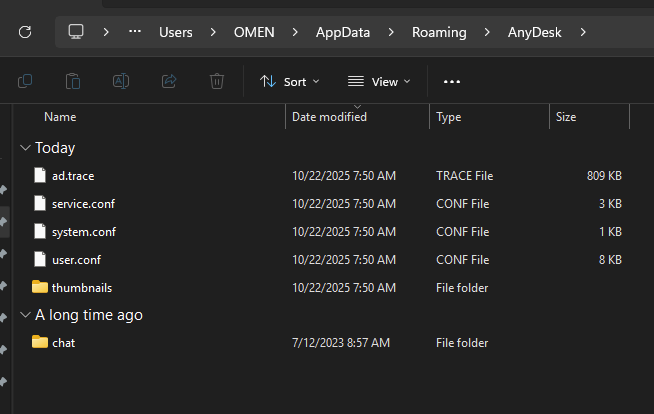
Knowing I was dealing with remote access and data exfiltration, the AnyDesk installation stood out to me.
Question 7
What is the IP address of the attacker?
Answer 7
Any details left by the attackers exfiltrating data through AnyDesk would be in the folder in the screenshot above. So I went digging through each file to see what I could find. This helpful blog made my life a little easier when looking for traces of connections from external IP addresses.
Using the findstr command in powershell lead revealed the following:

Last updated