Insider Lab
CyberDefenders Endpoint Forensics Lab

Scenario
After Karen started working for ‘TAAUSAI,’ she began doing illegal activities inside the company. ‘TAAUSAI’ hired you as a soc analyst to kick off an investigation on this case.
You acquired a disk image and found that Karen uses Linux OS on her machine. Analyze the disk image of Karen’s computer and answer the provided questions.
For this scenario, I had to set up a Windows 11 VM. Since FTK Imager seems to be unavailable on Linux. This will be my first time using FTK.
Question 1
Which Linux distribution is being used on this machine?
Answer 1
Looking under the boot folder, you can see that the host was running Kali.
Press enter or click to view image in full size

Question 2
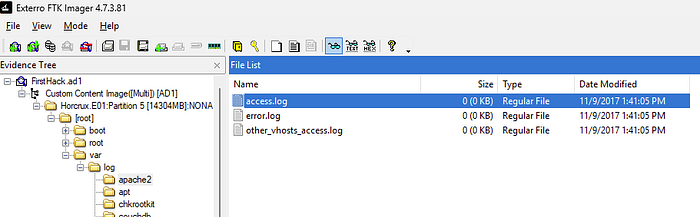
What is the MD5 hash of the Apache access.log file?
Answer 2
Looking through the system files, there is a log directory that holds apache2. From here I exported the access.log file and grabbed the MD5 hash: d41d8cd98f00b204e9800998ecf8427e.
Press enter or click to view image in full size
Question 3
It is suspected that a credential dumping tool was downloaded. What is the name of the downloaded file?
Answer 3
Checking the downloads folder reveals a zip archive of a credential dumping tool called mimikatz_trunk.zip. mimikatz its a widely avaliable Windows security tool that is avaliable on github.
Press enter or click to view image in full size

Question 4
A super-secret file was created. What is the absolute path to this file?
Answer 4
While this had me a little stumped for a little while. I found out that the evidence tree only includes folders. After I made sure to check for files under root, I was able to find a .bash_history file that contained all the commands the user had been using. One of which was to create the SuperSecretFile.txt: /root/Desktop/SuperSecretFile.txt
Press enter or click to view image in full size

Question 5
What program used the file didyouthinkwedmakeiteasy.jpg during its execution?
Answer 5
Searching through the bash history a little further, I found the user used binwalk on the .jpeg file, to extract information from it.
Question 6
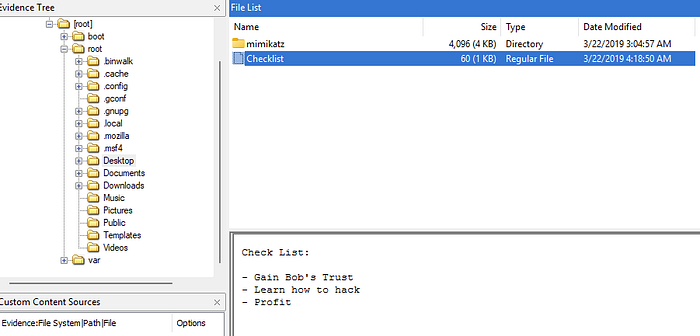
What is the third goal from the checklist Karen created?
Answer 6
After a little digging through the files, there was a file on the desktop named Checklist. Which gave me the answer: profit.
Press enter or click to view image in full size
Question 7
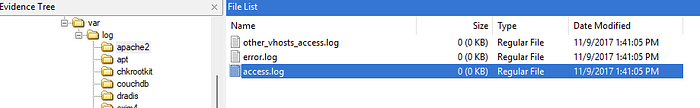
How many times was Apache run?
Answer 7
Checking through the logs, inside the apache2 folder. It appeared that it had never been run at all. All log files were empty which stuck out as strange. The answer here being 0.
Press enter or click to view image in full size
Question 8
This machine was used to launch an attack on another. Which file contains the evidence for this?
Answer 8
Looking through the file system, there are a couple of suspicious image files. One of which looks to be a screenshot of a desktop that was taken on execution of an .exe file called aylmao.exe. Which might indicate a remote access trojan. The file name in question is: irZLAohL.jpeg
Press enter or click to view image in full size

Question 9
It is believed that Karen was taunting a fellow computer expert through a bash script within the Documents directory. Who was the expert that Karen was taunting?
Answer 9
Checking the only folder in Documents, its revealed they were trying to create a script via bash. One of which gave the answer: Young.
Press enter or click to view image in full size

Question 10
A user executed the su command to gain root access multiple times at 11:26. Who was the user?
Answer 10
Switching users using a su command to gain root access should show up in authentication logs. Following this trail led me to the auth.log file under the var directory. Scrolling a little while until I found an su command being exectued, I could see that the user postgres was using said command.
Press enter or click to view image in full size

Question 11
Based on the bash history, what is the current working directory?
Answer 11
Going back to the bash_history file, it showed that someone had used the cd command to change the current working directory to /root/Documents/myfirsthack/

Last updated