PhishStrike Lab
CyberDefenders Threat Intel Lab
Scenario
As a cybersecurity analyst at an educational institution, you receive an alert about a phishing email targeting faculty members. The email appears to be from a trusted contact and claims a $625,000 purchase, providing a link to download an invoice. Your task is to investigate the email using Threat Intel tools. Analyze the email headers and inspect the link for malicious content. Identify any Indicators of Compromise (IOCs) and document your findings to prevent potential fraud and educate faculty on phishing recognition.
Question 1
Identifying the sender’s IP address with specific SPF and DKIM values helps trace the source of the phishing email. What is the sender’s IP address that has an SPF value of softfail and a DKIM value of fail?
Answer 1
SPF stands for sender policy framework. Which is an email authentication method to ensure the sending email server is authorized to originate from the email senders domain.
DKIM stands for DomainKey Identified Mail. Which enables domain owners to automatically sign emails from their domain. A cryptographic way to verify the email came from the domain.
The email tries to use the IP address 18.208.22.104 for the SPF authentication, but it softfails.
Press enter or click to view image in full size

Question 2
Understanding the return path of an email is essential for tracing its origin. What is the return path specified in this email?
Answer 2
Looking at the basic headers a .edu email was specified:
Press enter or click to view image in full size

Question 3
Identifying the source of malware is critical for effective threat mitigation and response. What is the IP address of the server hosting the malicious file related to malware distribution?
Answer 3
I looked into the plain text of the email. Within its body you can see hyperlinks to the malicious file, which contained the IP address.
Question 4
Identifying malware that exploits system resources for cryptocurrency mining is critical for prioritizing threat mitigation efforts. The malicious URL can deliver several malware types. Which malware family is responsible for cryptocurrency mining?
Answer 4
I used the website URLhaus for this answer, pasting in the IP address and looking at the payloads associated with it. Noticing CoinMiner was listed, giving me the answer!
Press enter or click to view image in full size

Question 5
Identifying the specific URLs malware requests is key to disrupting its communication channels and reducing its impact. Based on the previous analysis of the cryptocurrency malware sample, what does this malware request the URL?
Answer 5
On the same page as the answer above, there is a SHA256 hash.
Putting this into VirusTotal and looking at the relations tab gave me a couple of connected URLs. The first of which giving me the answer.
Question 6
Understanding the registry entries added to the auto-run key by malware is crucial for identifying its persistence mechanisms. Based on the BitRAT malware sample analysis, what is the executable’s name in the first value added to the registry auto-run key?
Answer 6
The malware was also tagged as BitRAT, so using the SHA256 of the malware and viewing it on Malware Bazaar, I was able to find an Any.Run report that detailed the registry edit.

Question 7
Identifying the SHA-256 hash of files downloaded from a malicious URL is essential for tracking and analyzing malware activity. Based on the BitRAT analysis, what is the SHA-256 hash of the file previously downloaded and added to the autorun keys?
Answer 7
This question is a little backwards, because I needed the SHA256 hash in the previous question.
Question 8
Analyzing the HTTP requests made by malware helps in identifying its communication patterns. What is the URL in the HTTP request used by the loader to retrieve the BitRAT malware?
Answer 8
Going back to VirusTotal, there was a second contacted URL that was present in the result.
Question 9
Introducing a delay in malware execution can help evade detection mechanisms. What is the delay (in seconds) caused by the PowerShell command according to the BitRAT analysis?
Answer 9
The malware inputs a base64 at runtime into powershell to execute a 50 second sleep.
Press enter or click to view image in full size
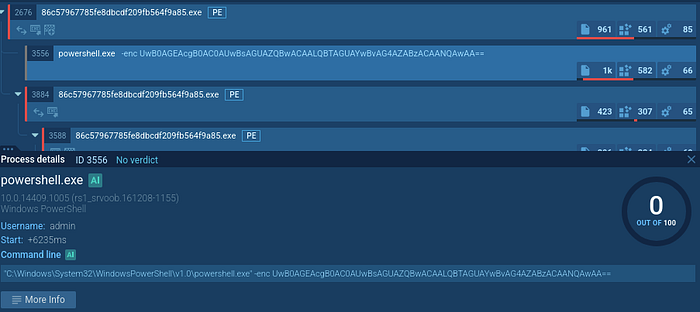
I used CyberChef to decode the base64 to give me the following:

Question 10
Tracking the command and control (C2) domains used by malware is essential for detecting and blocking malicious activities. What is the C2 domain used by the BitRAT malware?
Answer 10
The community tab in the VirusTotal result listed the C2 server that the malware uses.

Questions 11
Understanding how malware exfiltrates data is essential for detecting and preventing data breaches. According to the AsyncRAT analysis, what is the Telegram Bot ID used by this malware?
Answer 11
For this answer, I had to look through various malware analysis reports. The one that was most useful and gave me the answer was the tria.ge.
Press enter or click to view image in full size


Last updated