GrabThePhisher Lab
CyberDefenders Threat Intel Lab

Scenario
A decentralized finance (DeFi) platform recently reported multiple user complaints about unauthorized fund withdrawals. A forensic review uncovered a phishing site impersonating the legitimate PancakeSwap exchange, luring victims into entering their wallet seed phrases. The phishing kit was hosted on a compromised server and exfiltrated credentials via a Telegram bot.
Your task is to conduct threat intelligence analysis on the phishing infrastructure, identify indicators of compromise (IoCs), and track the attacker’s online presence, including aliases and Telegram identifiers, to understand their tactics, techniques, and procedures (TTPs).
Question 1
Which wallet is used for asking the seed phrase?
Answer 1
There are various different wallet services that people can use when transacting with Crypto. One of the more popular and relevant ones here is MetaMask.
Question 2
What is the file name that has the code for the phishing kit?
Answer 2
The compromised file wasn’t hard to track down:

Question 3
In which language was the kit written?
Answer 3
The file is written in PHP.
Question 4
What service does the kit use to retrieve the victim’s machine information?
Answer 4
Within the MetaMask.php file, there is a link to an API from a service called: sypex geo.

Question 5
How many seed phrases were already collected?
Answer 5
Looking deeper into the code, it appears that it logs the secret phrases in plaintext in a file called log.txt.
Press enter or click to view image in full size

Opening said file reveals 3 seed phrases.
Press enter or click to view image in full size

Question 6
Could you please provide the seed phrase associated with the most recent phishing incident?
Answer 6
The very last line of text within log.txt is the latest seed phrase.
Question 7
Which medium was used for credential dumping?
Answer 7
A Telegram bot was used to dump the credentials
Press enter or click to view image in full size

This is a very common method when trying to extract credentials.
Question 8
What is the token for accessing the channel?
Answer 8
The above image provides the token, within the function called sendTel.
Question 9
What is the Chat ID for the phisher’s channel?
Answer 9
Same as the answer above, the id is the first line of code within sendTel.
Question 10
What are the allies of the phish kit developer?
Answer 10
It appears that the dev made a mistake in leaving a small trail for people to potentially follow. Leaving any sort of username/handle in malicious code is bad opsec.

Question 11
What is the full name of the Phish Actor?
Answer 11
This is where I believe the lab has become broken. Any attempt to use the Telegram API to retrieve the data required, via a browser or a command line, returns an unauthorized error code.
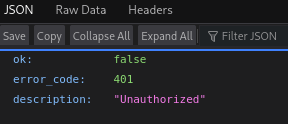
The answer is: Marcus Aurelius. I did sadly have to get this from the official write up.
Question 12
What is the username of the Phish Actor?
Answer 12
Same as above. Sadly I had to get this answer from the official write up. I am not sure if I was doing something wrong, but it does appear to be broken. Answer: pumpkinboii
Last updated