IceID Lab
CyberDefenders Threat Intel Lab
Scenario
A cyber threat group was identified for initiating widespread phishing campaigns to distribute further malicious payloads. The most frequently encountered payloads were IcedID. You have been given a hash of an IcedID sample to analyze and monitor the activities of this advanced persistent threat (APT) group.
Question 1
What is the name of the file associated with the given hash?
Answer 1
This strain of malware seems to be a Office XML Spreadsheet, using the name: document-1982481273.xlsm
Question 2
Can you identify the filename of the GIF file that was deployed?
Answer 2
Looking at the various URLs that are connected to this malware, its clear that it drops a GIF called 3003.gif
Press enter or click to view image in full size

Question 3
How many domains does the malware look to download the additional payload file in Q2?
Answer 3
Going by the image above, the answer is 5.
Question 4
From the domains mentioned in Q3, a DNS registrar was predominantly used by the threat actor to host their harmful content, enabling the malware’s functionality. Can you specify the Registrar INC?
Answer 4
Looking through the connected domains, there appeared to be 2 registrars. NameCheap and Launchpad. The answer in this case was NameCheap.
Press enter or click to view image in full size

Question 5
Could you specify the threat actor linked to the sample provided?
Answer 5
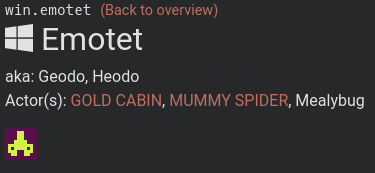
Looking through the VirusTotal page, the strain of the malware appears to be Emotet. Using this information, a quick search on malpedia led me to the answer: Gold Cabin.
Question 6
In the Execution phase, what function does the malware employ to fetch extra payloads onto the system?
Answer 6
Looking at the behaviour tab on VirusTotal you can see that the malware uses UrlDownloadToFileA to grab extra files.
Press enter or click to view image in full size


Last updated