CozyHosting Lab
Hack the Box Penetration Lab
Reconnaissance
First up, a port scan:
┌─[zero@parrot]─[~]
└──╼ $nmap -p- -sCV 10.10.11.230
Starting Nmap 7.94SVN ( https://nmap.org ) at 2024-02-05 11:19 PST
Nmap scan report for cozyhosting.htb (10.10.11.230)
Host is up (0.037s latency).
Not shown: 65471 closed tcp ports (conn-refused), 61 filtered tcp ports (no-response)
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 8.9p1 Ubuntu 3ubuntu0.3 (Ubuntu Linux; protocol 2.0)
| ssh-hostkey:
| 256 43:56:bc:a7:f2:ec:46:dd:c1:0f:83:30:4c:2c:aa:a8 (ECDSA)
|_ 256 6f:7a:6c:3f:a6:8d:e2:75:95:d4:7b:71:ac:4f:7e:42 (ED25519)
80/tcp open http nginx 1.18.0 (Ubuntu)
|_http-title: Cozy Hosting - Home
|_http-server-header: nginx/1.18.0 (Ubuntu)
1111/tcp open lmsocialserver?
Service Info: OS: Linux; CPE: cpe:/o:linux:linux_kernelThe scan revealed 3 TCP ports that were currently open: 22, 80 and 1111. Not knowing exactly what an lmsocialserver? was, I quickly google’d it, revealing some random 19 year of forum posts that didn’t tell me too much. From researching I know there are some nginx vulnerabilities and you can use a tool called nginxpwner. But I will dig further before trying anything.
Then a fuzz scan:
The first fuzz scan revealed that there were a decent number of pages to be explored: login, logout, admin, index and actuator. I then did a further fuzz scan on actuator since this one stood out to me as a none default page.
After doing so I found more pages that could possibly have a foothold within them: sessions, health, env and beans.
Before checking those out, I dug into the source code of the main page to see what it was built off of and if I could find anything of interest.
The first thing I noticed was it was made using a template called BoostrapMade and there was a direct link to the website. Although nothing really stood out to me.
Looking back at the URL paths I found, there was a strange occurance when visiting both /acuator/health and /acuator/env both appeared to have a somewhat broken endpoint which could be useful. However after looking at /acuator/sessions I found what appears to be a session cookie for a user called kanderson. This could be the foothold I was looking for, a session hijack using this new cookie.

After opening my inspect element and replacing my cookie with kanderson’s I was able to bypass the login screen and load into the admin dashboard.
Press enter or click to view image in full size

I did find that I was kicked out of the dashboard every so often. It seems the cookie became invalid after a certain amount of time. So I used a curl command in my terminal to grab a new cookie to carry on trying to find more of a foothold.
Interestingly I found there was a remote host connection tool. After entering a few random combinations of Hostname and Username I got a timeout error. The one that stood out to me was a HTTP Status 400 error,
Here are some of the errors that I got:
Press enter or click to view image in full size

I fired up BurpSuite to see what kinds of requests are being made when I am hitting the submit button. Entering a default IP address of 127.0.0.1 with no Username threw up this raw response in BurpSuite:

(Note, around this time I had made the switch to Kali from ParrotOS. Kali seems so much quicker and the UI is a lot sleeker.)
Judging by line 5 the backend was trying to execute the command directly with a SSH which could be prime for manipulation. Admittedly at this point I was a little stuck. Looking at another write up online I found if you put an ‘ after the username you can trigger something to make sure it’s a bash shell.

Accessing the system
Now to create a bash file in order to get a reverse shell, then attempt to get a stable shell after that. This is the bash file that I would attempt to upload to their side of the server. I chose a port number and set up a listener.
Press enter or click to view image in full size

After converting my payload to base64 and copy-pasting it into the username section I was about to gain access to the shell. I then needed to make it a stable shell.

To gain a more stable shell I used this python script, note do this every single time you log back in:
After doing this I now just poke around a little and see who I am, what IDs there are and what files are under the current dir.

It looks like there is a .jar file that would be nice to dig into. I then set up a listener on the target machine for me to then grab the file from my machine using wget.
Press enter or click to view image in full size


After a brief search using jd-gui, I have found the username and password to a database called “cozyhosting”. Now after logging back into the machine using the same steps above.
The machine was very slow at this point and would constantly be stuck loading even when in the machine itself, I ended up switching vpns on HTB to TCP. This seems to have fixed the connectivity issues.
I went ahead and did a little research on how to interact with a postgres database. I used the following to attempt to login:
After using the password to login, I was able to connect to the cozyhosting database and view the contents of the users column. This revealed a hash of the passwords for both “kanderson” and “admin”. Next step, using John the Ripper to crack this password.

I copy and pasted the admin’s hashed password into a txt called hash. Next I ran John and used the list called rockyou.txt, revealing the password below:
Press enter or click to view image in full size

So with this password I attempted to login using the username admin then the password that I had just cracked. Sadly the username admin didn’t exist, so this password must belong to someone else. I chose to list the dir in the home dir to see if I could find another username.
Press enter or click to view image in full size

Turns out there is a user called “josh”. Now let’s try and login using his username and the password we got earlier. Success! We logged in using that combination of username and password. Exploring their files I find the user flag in a file called user.txt!
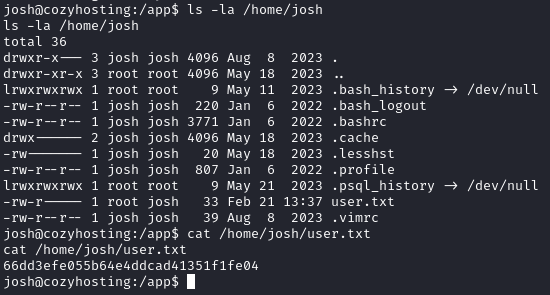
The final root flag was a little tricky, I didn’t know how to get root access from the shell. So after a little research, it looks like if the current user can use all commands in ssh as root, then there is a small payload that can be used to secure the access: https://gtfobins.github.io/gtfobins/ssh/#sudo.
Press enter or click to view image in full size

After that it was a pretty simple hunt for the flag: root/root.txt!
Conclusion
This took me quite a while to complete. I got stuck when creating the bash reverse shell script. I had one noted down from some of the HTB tutorials, but didn’t know you had to convert it to URL encoded key chars. Which can be done in BurpSuite. PSQL was also something I was not familiar with, so looking up the documentation for that and some examples really helped.
Speaking of BurpSuite, I learned a lot more about using its basic functionality. I am still not 100% confident on using it to send a response. But using the fields on the website I was about to manually do it. I am sure later down the line I will need to use it to inject code, so that will be a good learning experience.
Overall I am pretty happy with my first box, it took a little bit of research and help from another user’s write-up, but learning a lot and making plenty of notes for the future is always good.
Last updated