Brave Lab
CyberDefenders Memory Forensic Lab

Scenario
A memory image was acquired from a suspected compromised Windows workstation. The system belonged to a user flagged for potentially malicious activities, including unauthorized access attempts and unusual browsing patterns. The security team observed network activity to external IPs associated with encrypted communication services.
Your task is to analyze the provided memory dump to uncover details about the processes involved, identify active connections at the time of the compromise, and trace the usage patterns of specific applications.
Question 1
What time was the RAM image acquired according to the suspect system?
Answer 1
Running the image through Volatility 3 using the following command, I was able to determine a tone of information about the machine the memory dump was from.
Giving me the following answer: 2021–04–30 17:52:19
Question 2
What is the SHA256 hash value of the RAM image?
Answer 2
A simple SHA256 command in the terminal gave me this:
Question 3
What is the process ID of brave.exe?
Answer 3
With a combination of grep and windows.pslist I was able to quickly determine the answer:
Question 4
How many established network connections were there at the time of acquisition?
Answer 4
Using the same method, but this time using netscan along with grep I found the answer to be 10 established connections.
Question 5
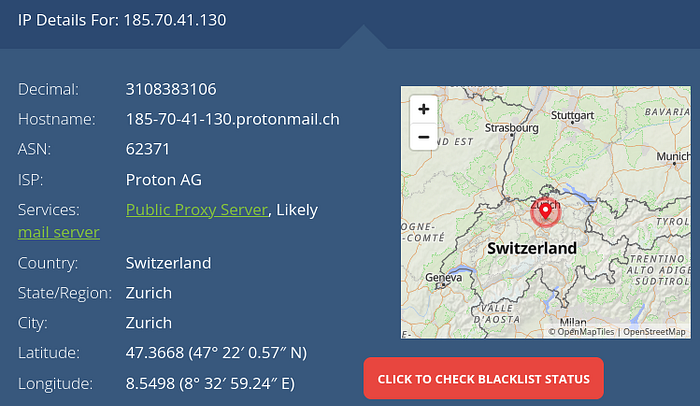
Which domain name does Chrome have an established network connection with?
Answer 5
Looking into the established connections that chrome.exe was making, reveled only 1. An IP address, 185.70.41.130, linked to protonmail.ch.
Press enter or click to view image in full size
Question 6
What is the MD5 hash value of the process executable for PID 6988?
Answer 6
Looking through the process output revealed the executable file with the PID 6988 was named OneDrive.exe. I however first went about this the wrong way, I first tried to dump all the files to get the OneDrive.exe. However when I grabbed that versions MD5 hash value, it was coming back as incorrect.
The alternative method, is to grab the file straight from the process list using the following:
This dumps the exe straight from the process list itself, giving me the correct answer when I ran an MD5sum command on it.
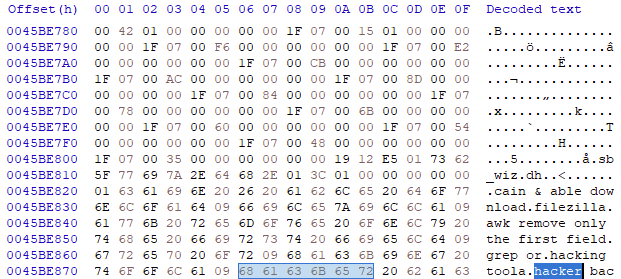
Question 7
Can you identify the word that begins at offset 0x45BE876 and is 6 bytes long?
Answer 7
Using the tool HxD you can go to a specific offset by pressing CTRL+G. Then from there I entered the offset 45BE876 and found following:
Question 8
What is the creation date and time of the parent process of powershell.exe?
Answer 8
Using the process tree command back on my Kali box, I got the following output:
userinit.exe is the parent process in this situation.
Question 9
What is the full path and name of the last file opened in notepad?
Answer 9
Using the process tree I can get an idea of what notepad.exe was doing at the time of the capture. The following is the results:
Question 10
How long did the suspect use Brave browser? (In Hours)
Answer 10
Using the windows.registry.userassist plugin for Volatility gave me a clear answer of 4 hours.

Last updated